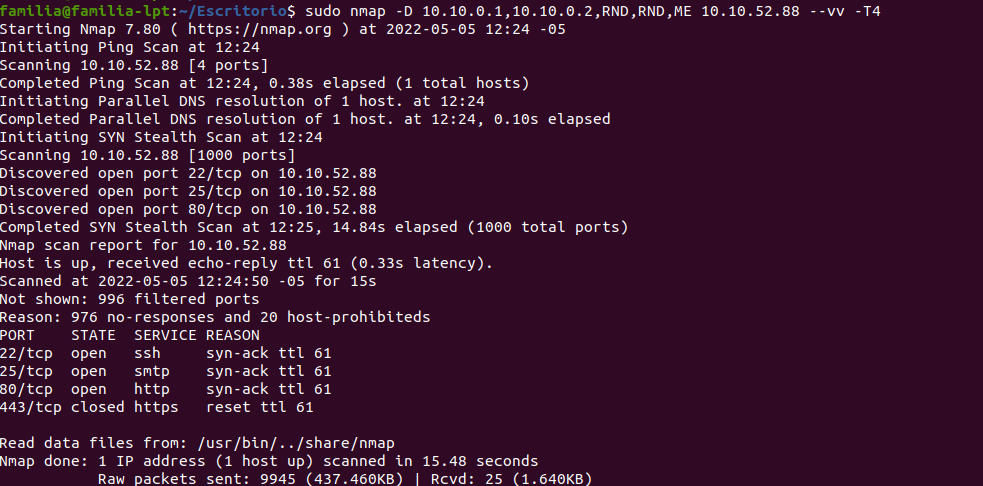
Evading Firewall/IDS during network reconnaissance using nmap | by Prateek Parashar | InfoSec Write-ups

Understanding Network Deception Technology - S2720, S5700, and S6720 V200R013C00 Configuration Guide - Network Management and Monitoring - Huawei
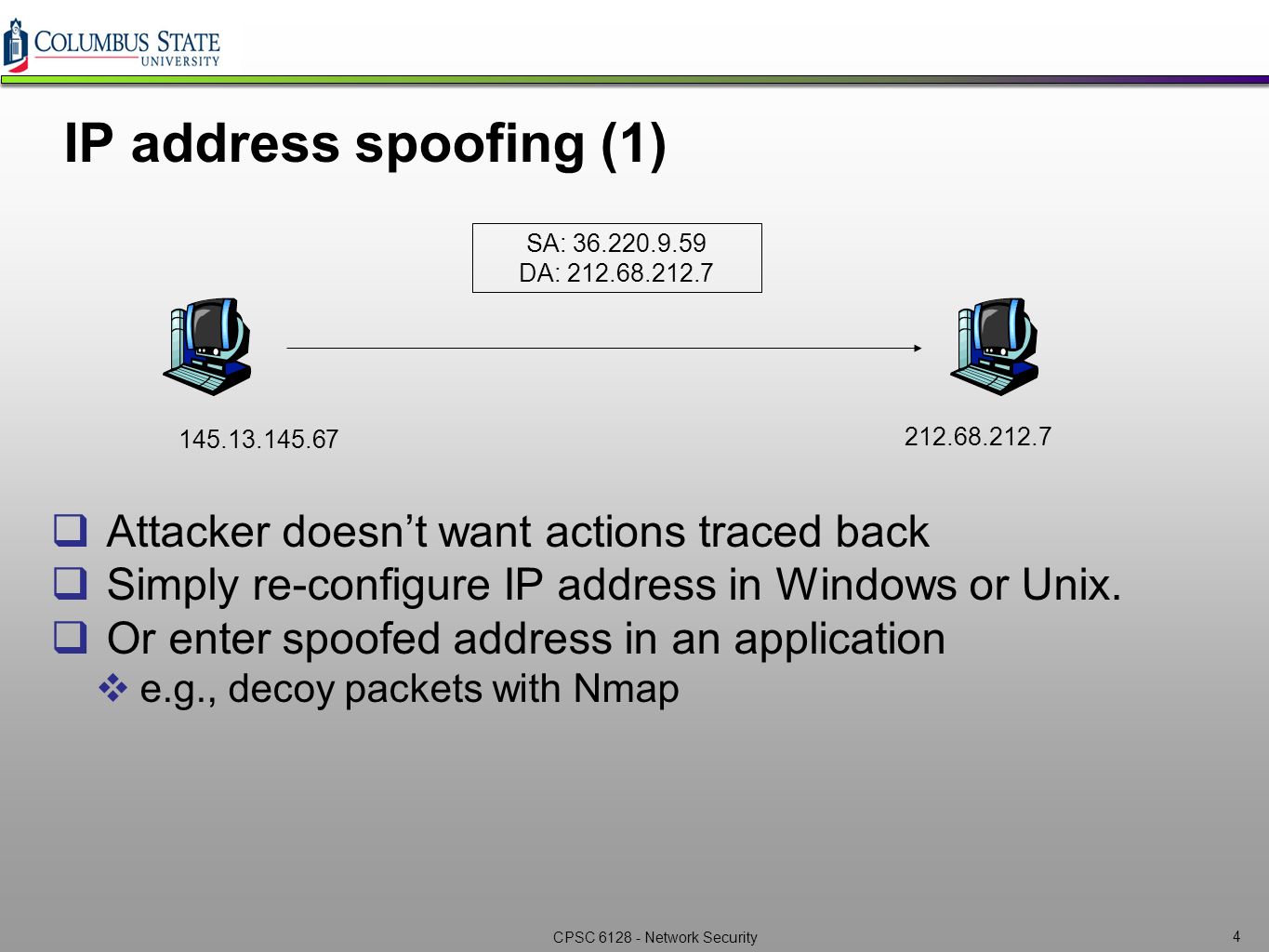



![PDF] DESIR: Decoy-enhanced seamless IP randomization | Semantic Scholar PDF] DESIR: Decoy-enhanced seamless IP randomization | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/9717a11ab27724e5cf447ec705e965be509290dc/2-Figure1-1.png)